创建 VPC
vpc 地址范围为 192.168.0.0/16
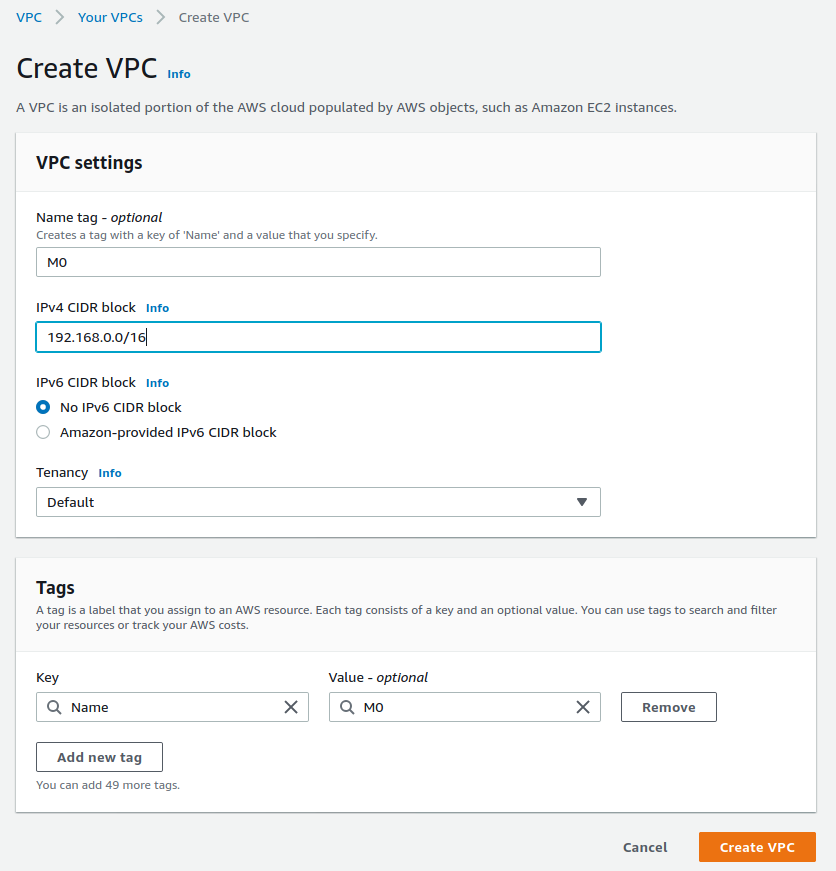
新建 vpc 详细信息如下 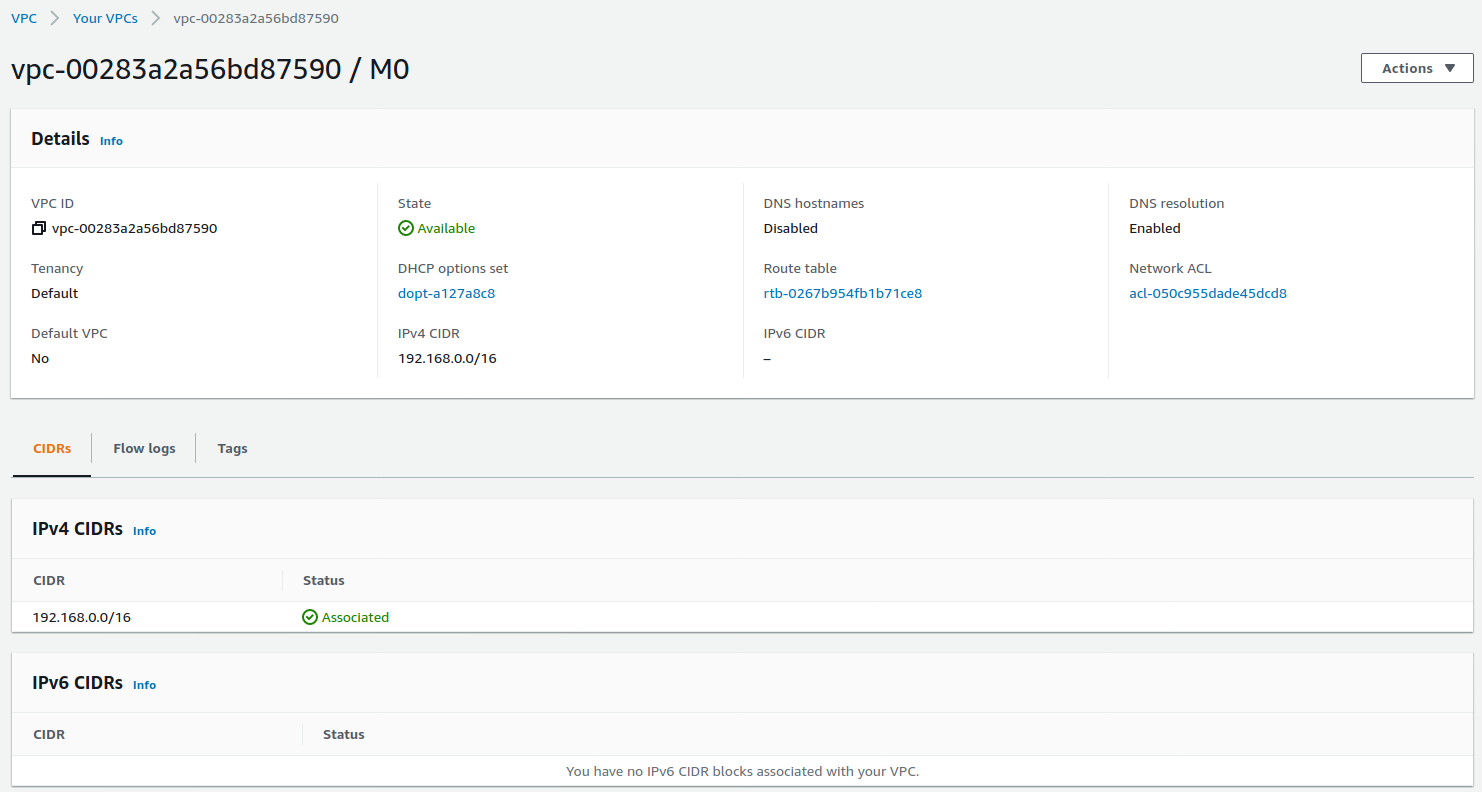
创建两个子网
M0-0 : 192.168.0.0/24
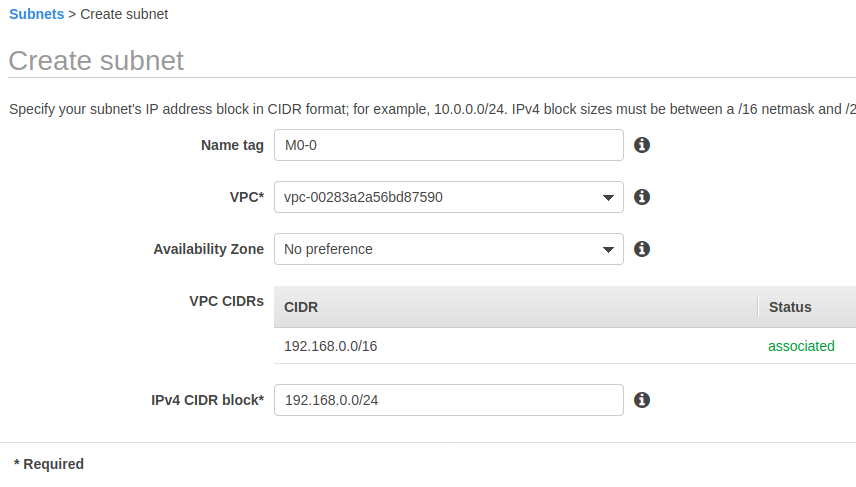
M0-1 : 192.168.1.0/24

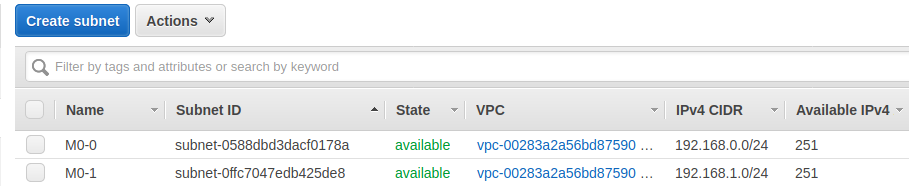
子网详细信息
创建互联网网关
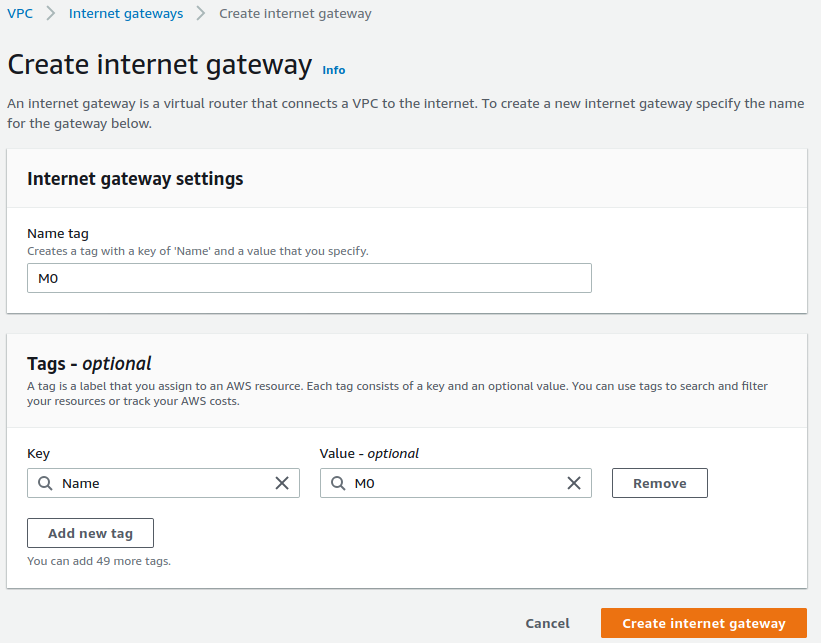
选择 Actions -> Attach to VPC 将网关附加到 VPC M0
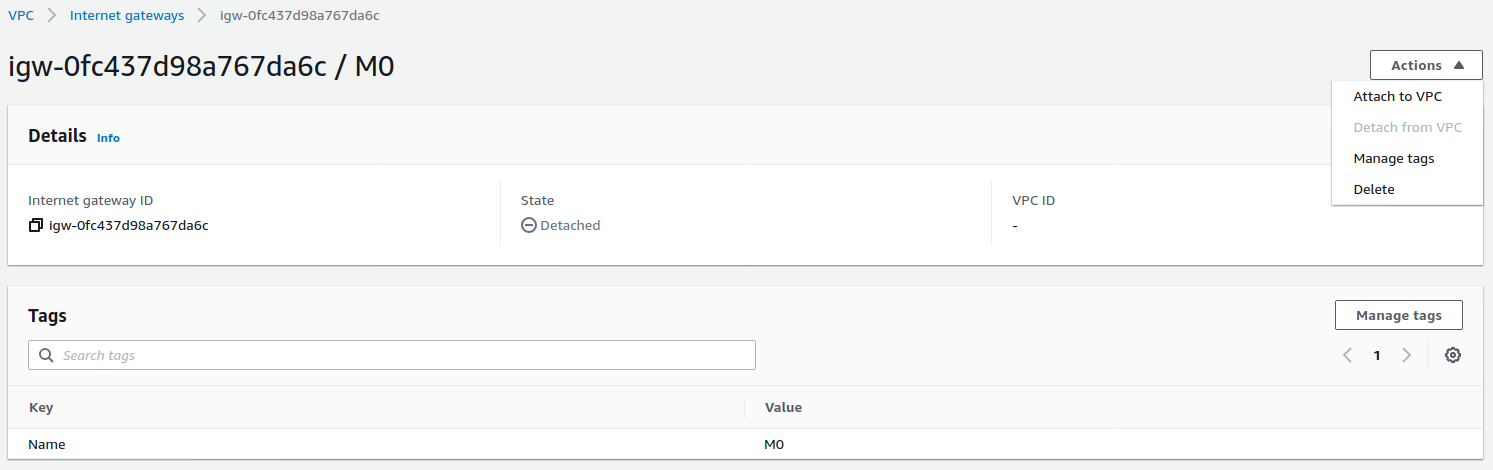
网关附加到 VPC M0
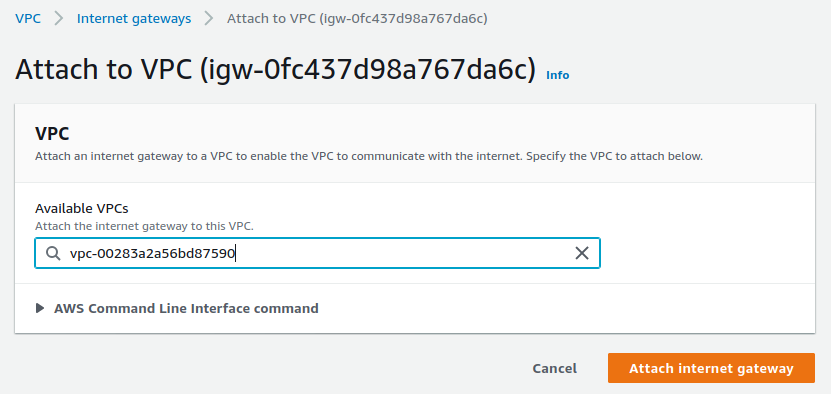
新建立路由表
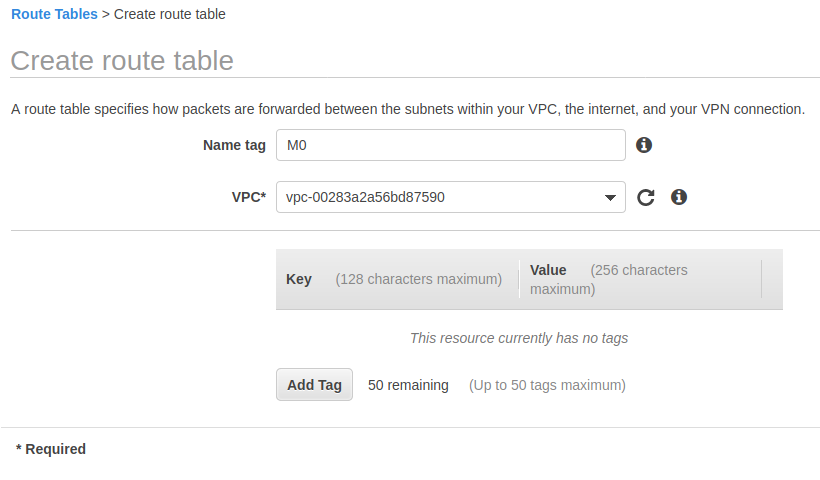
新建立的路由表默认只有一条规则,用于 VPC 内部
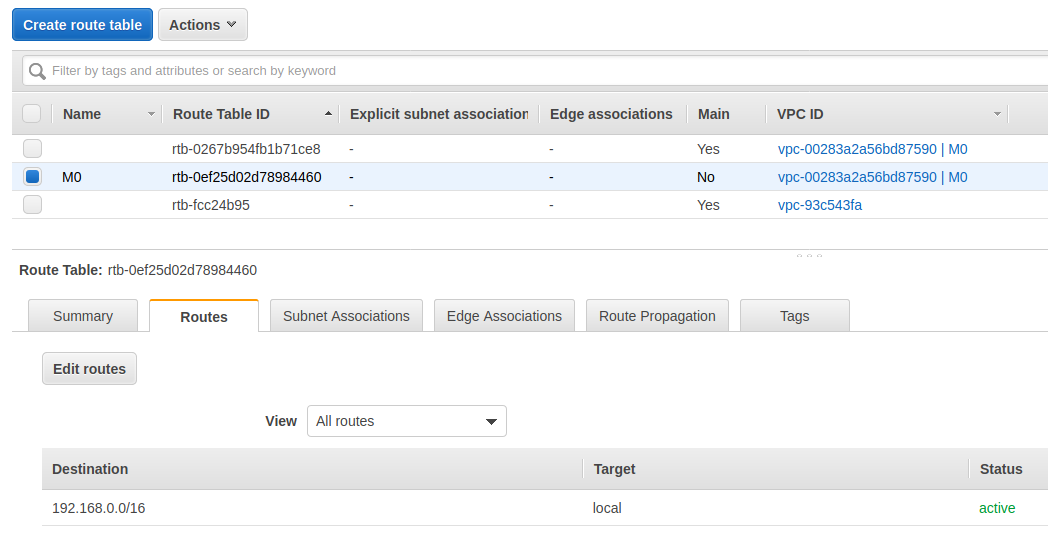
添加一条路由规则,将流向 VPC 外的流量发送到互联网网关
Destination:0.0.0.0/0Target: 之前创建的互联网网关
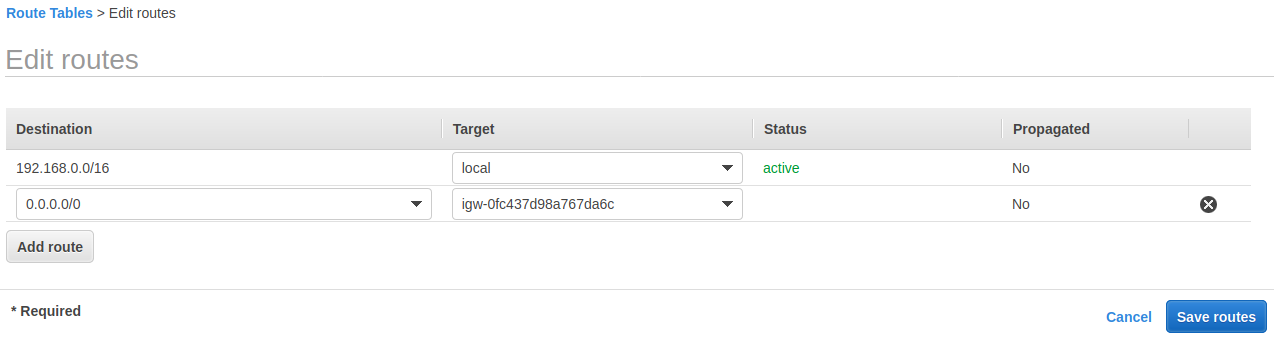
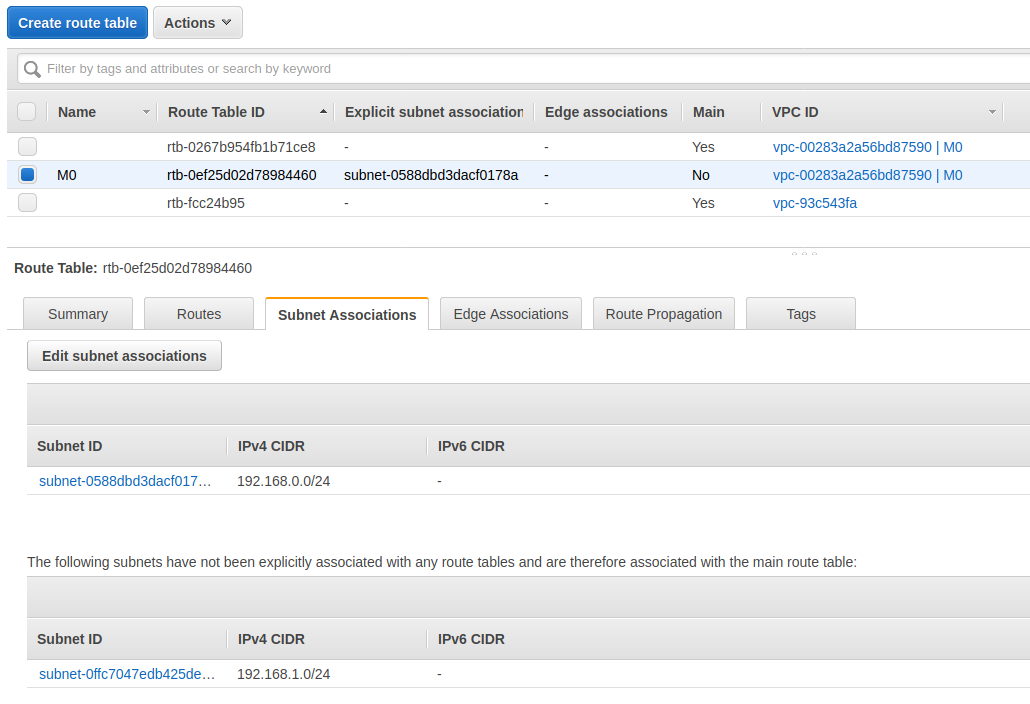
添加规则后的路由表
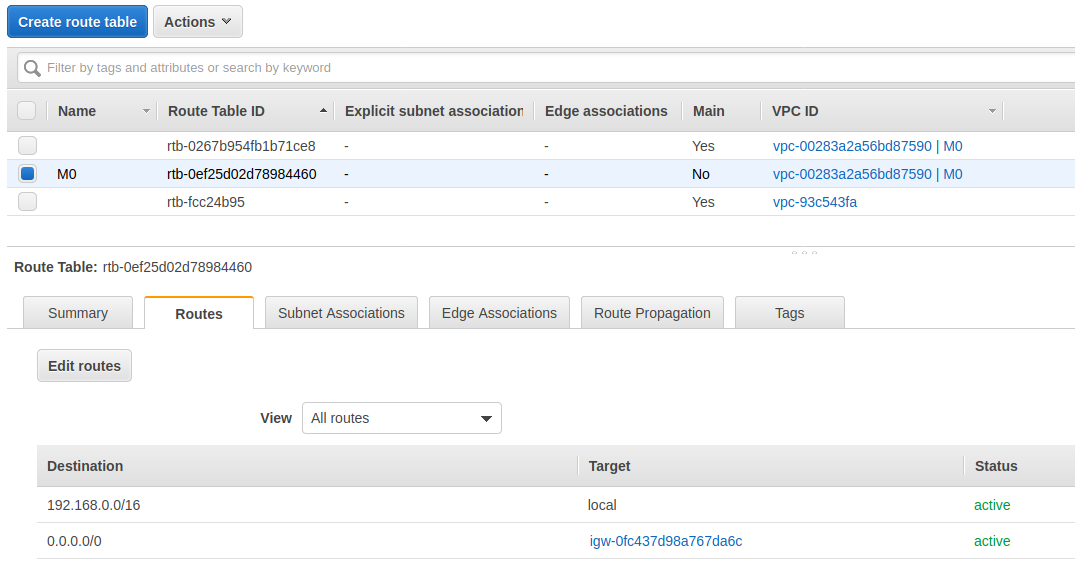
将路由表关联 M0-0 子网,使得该子网能够访问公网
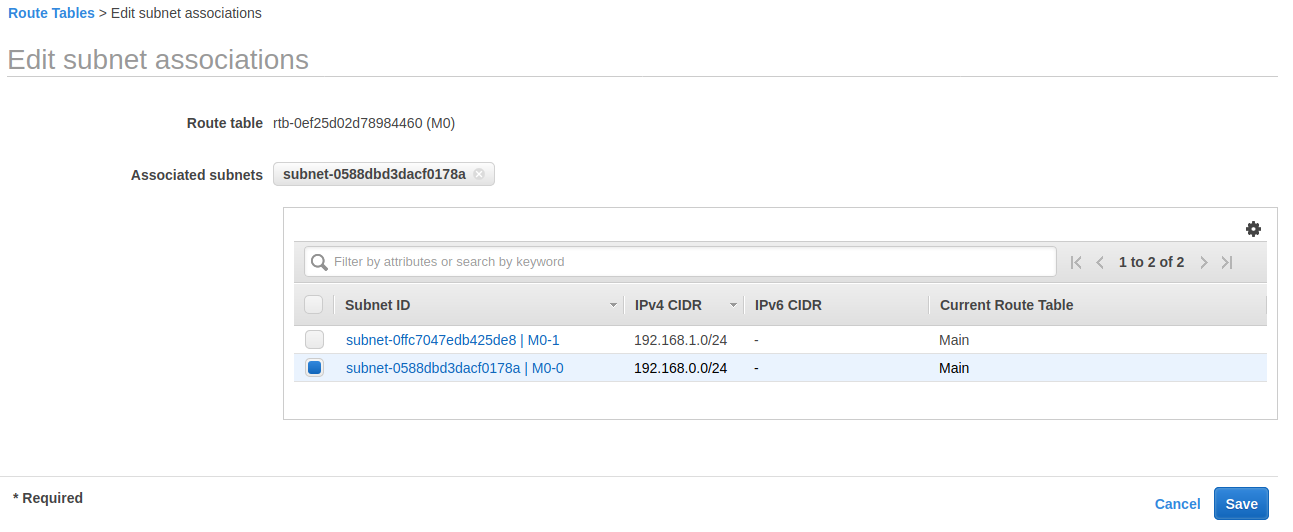
关联子网后的路由表
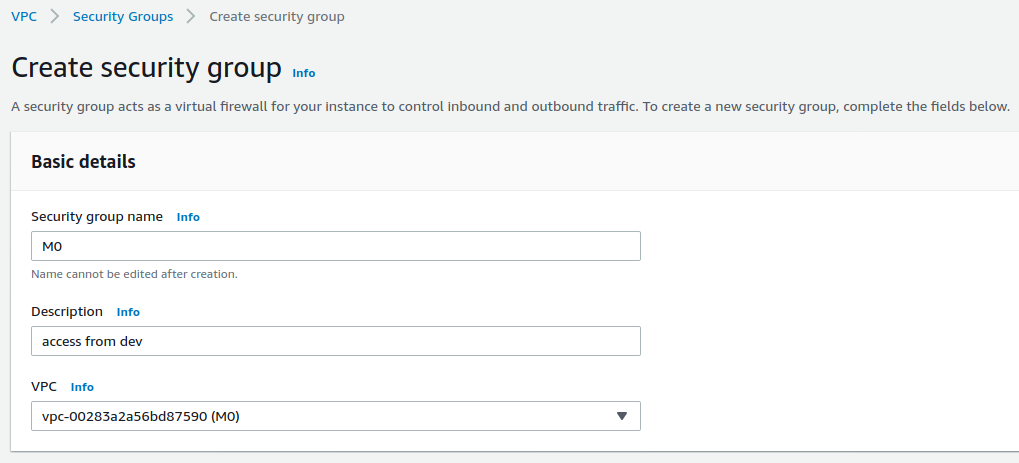
创建公网 Security Group
在 VPC M0 上创建一个 Security Group
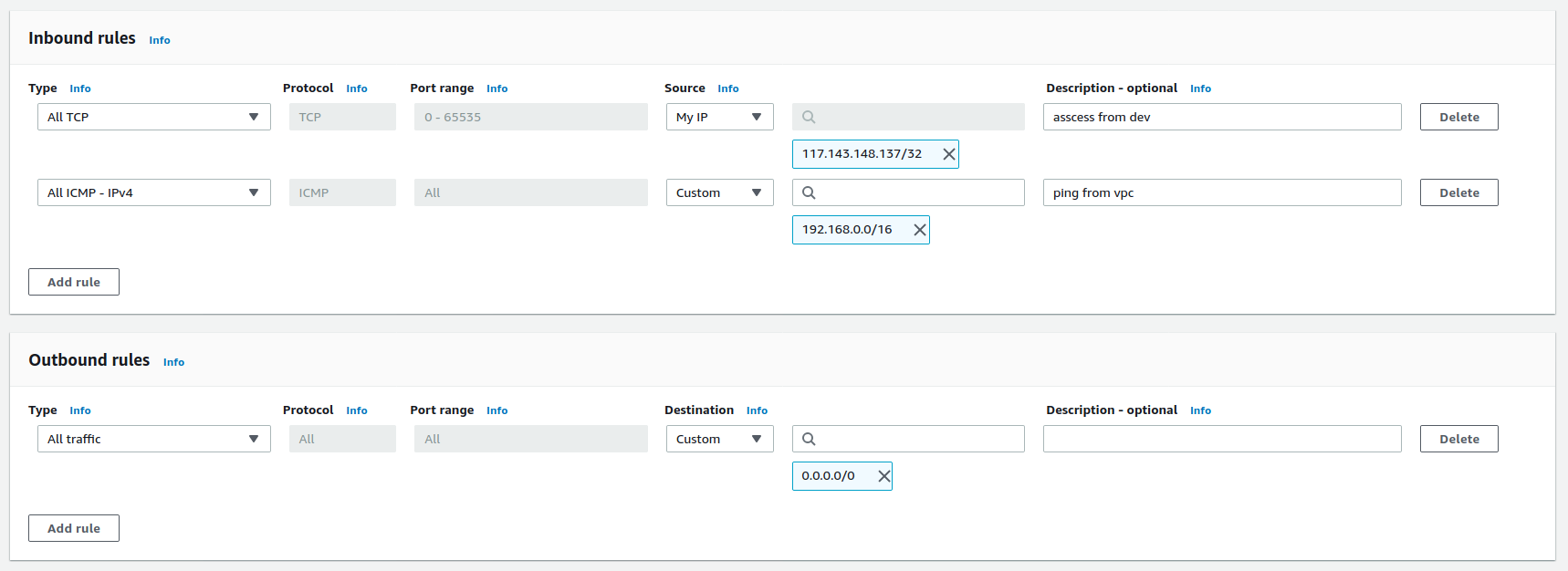
Security Group 的规则如下
- 允许来自当前开发机器的所有
TCP链接 - 允许来自
VPC内部的ICMP-IPv4,用于ping测试
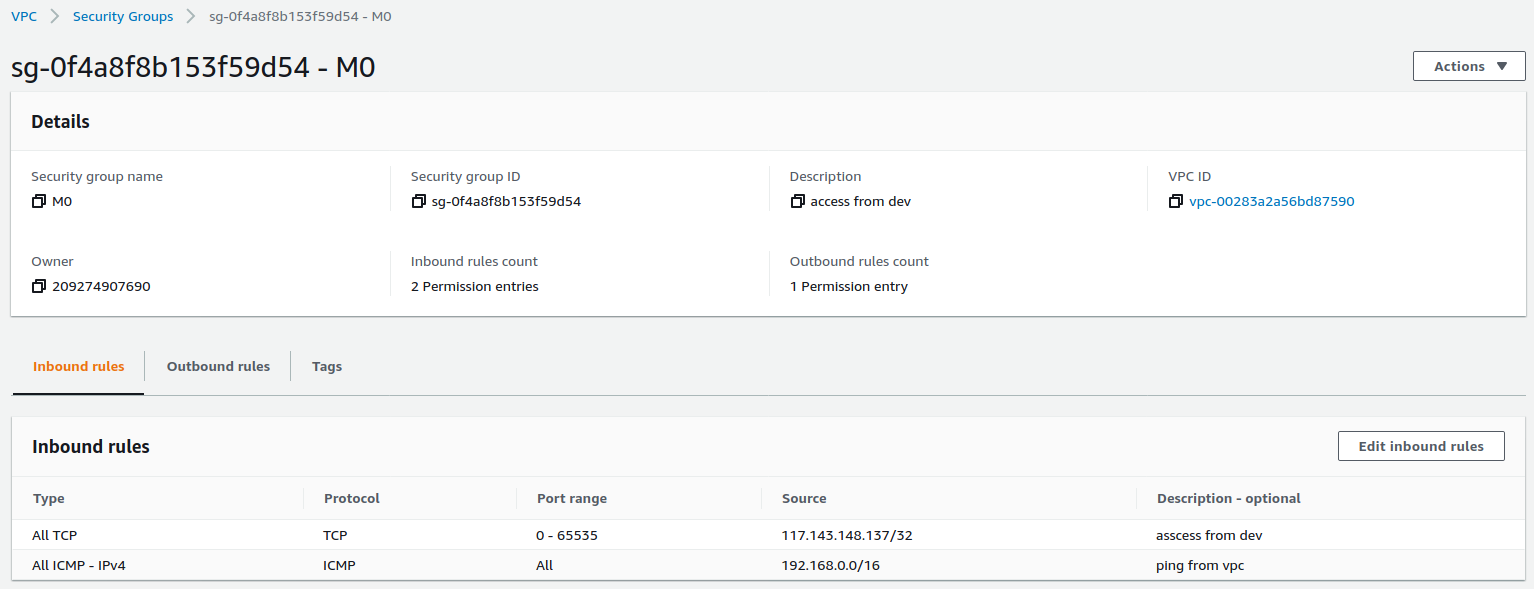
Security Group 详细信息
创建 NAT 实例
AMI 选择最新的 NAT Image
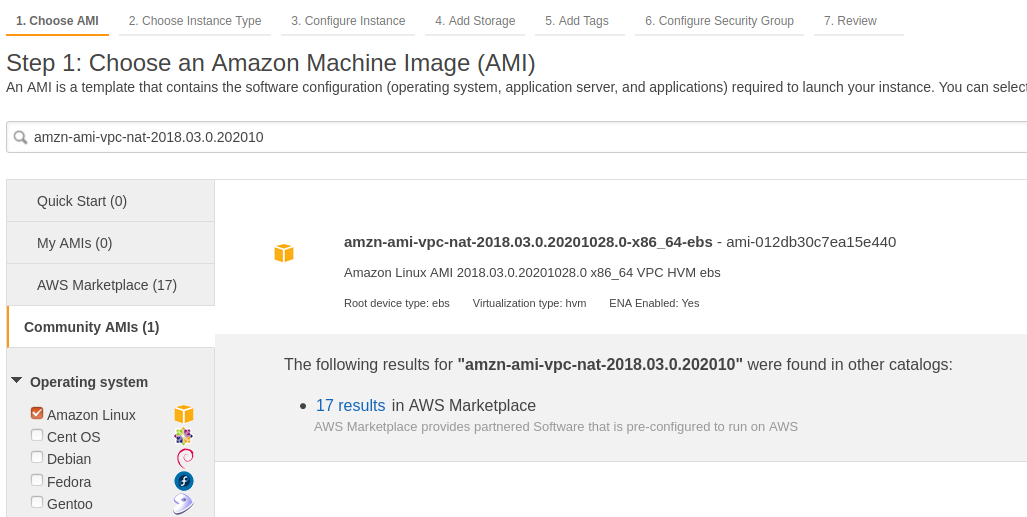
选择实例类型,本次演示选择 t2.micro
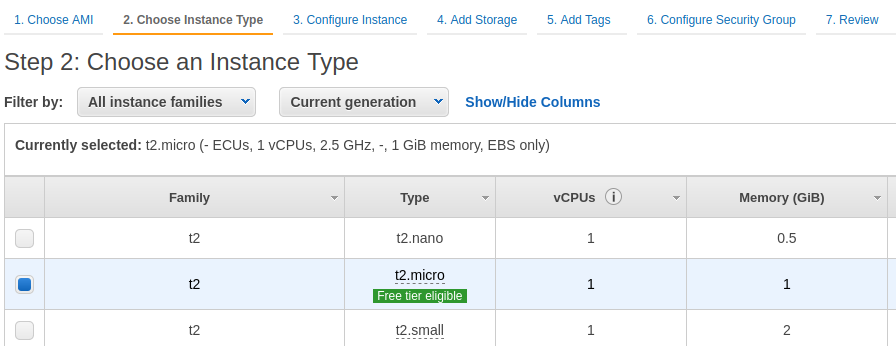
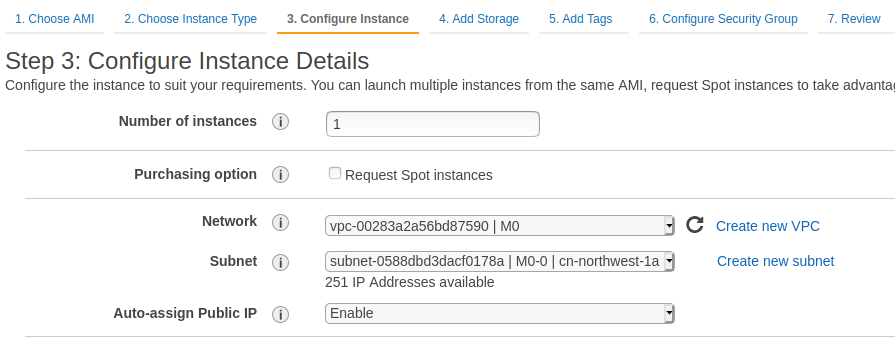
配置实例:
Network: 选择VPC M0Subnet: 选择M0-0Auto-assign Public IP:Enable
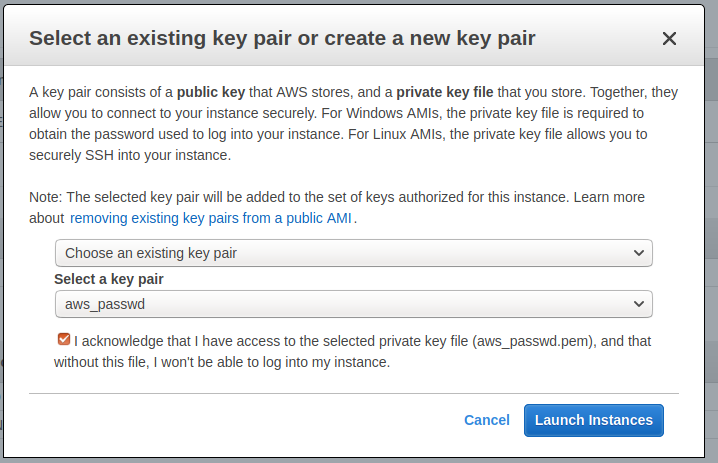
添加标签 Name -> M0-0-0

Security Group 选择之前创建的 M0

选择一个 key pair,然后启动实例
禁用 NAT 实例的 SrcDestCheck 属性
依次选择 NAT 实例 M0-0-0 -> Actions -> Networking -> Change Source/Dest.Check
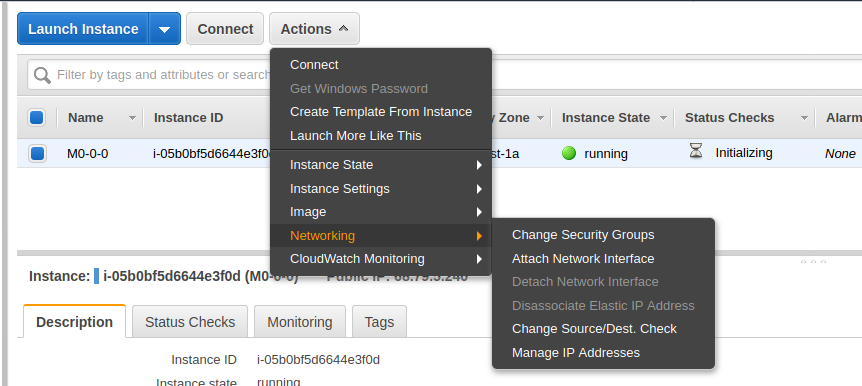
选择 Yes, Disable
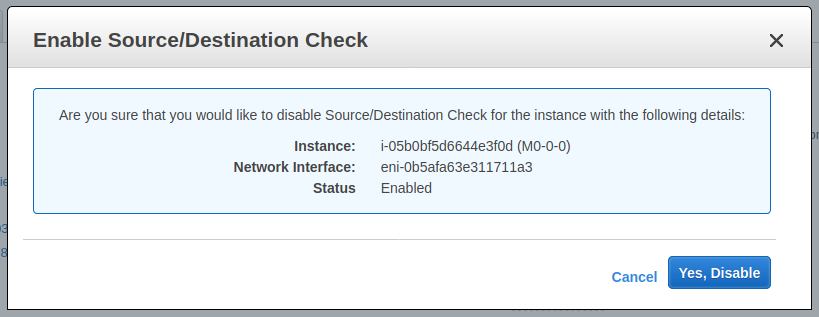
NAT 实例详细信息
- 公网
IP为68.79.5.240
SSH 远程登录 M0-0-0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ ssh -i ~/.ssh/aws_passed.pem ec2-user@68.79.5.240
The authenticity of host '68.79.5.240 (68.79.5.240)' can't be established.
ECDSA key fingerprint is SHA256:Z14wTfP8Yl2nCuAASW4LXyNflgTOEtnR46dtsKGZ2Zo.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '68.79.5.240' (ECDSA) to the list of known hosts.
__| __|_ )
_| ( / Amazon Linux AMI
___|\___|___|
https://aws.amazon.com/amazon-linux-ami/2018.03-release-notes/
[ec2-user@ip-192-168-0-6 ~]$ ping www.baidu.com
PING www.a.shifen.com (220.181.38.150) 56(84) bytes of data.
64 bytes from 220.181.38.150: icmp_seq=1 ttl=46 time=20.2 ms
64 bytes from 220.181.38.150: icmp_seq=2 ttl=46 time=20.2 ms
64 bytes from 220.181.38.150: icmp_seq=3 ttl=46 time=20.3 ms
更新 VPC M0 主路由表
选择 M0 的主路由表,添加规则:流向外网的所有流量路由到 NAT 实例
Destination:0.0.0.0/0流向外网的所有流量Target: 选择创建的NAT实例M0-0-0
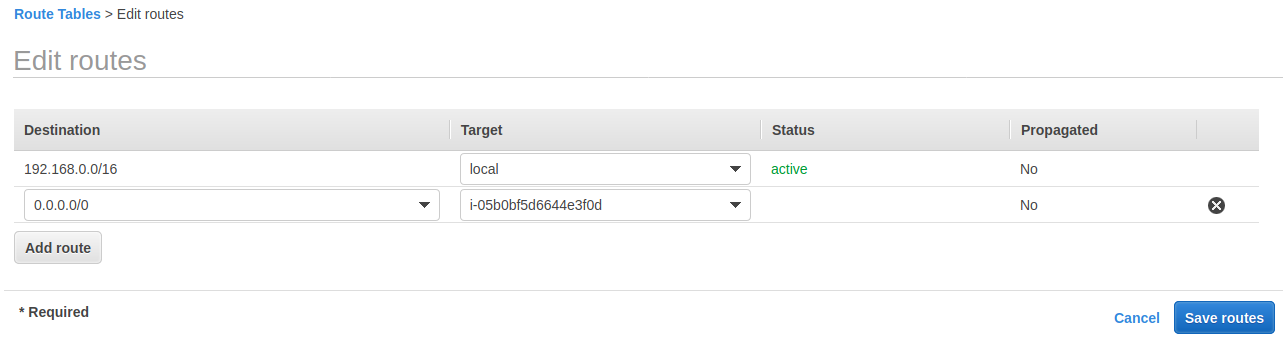
主路由表详细信息
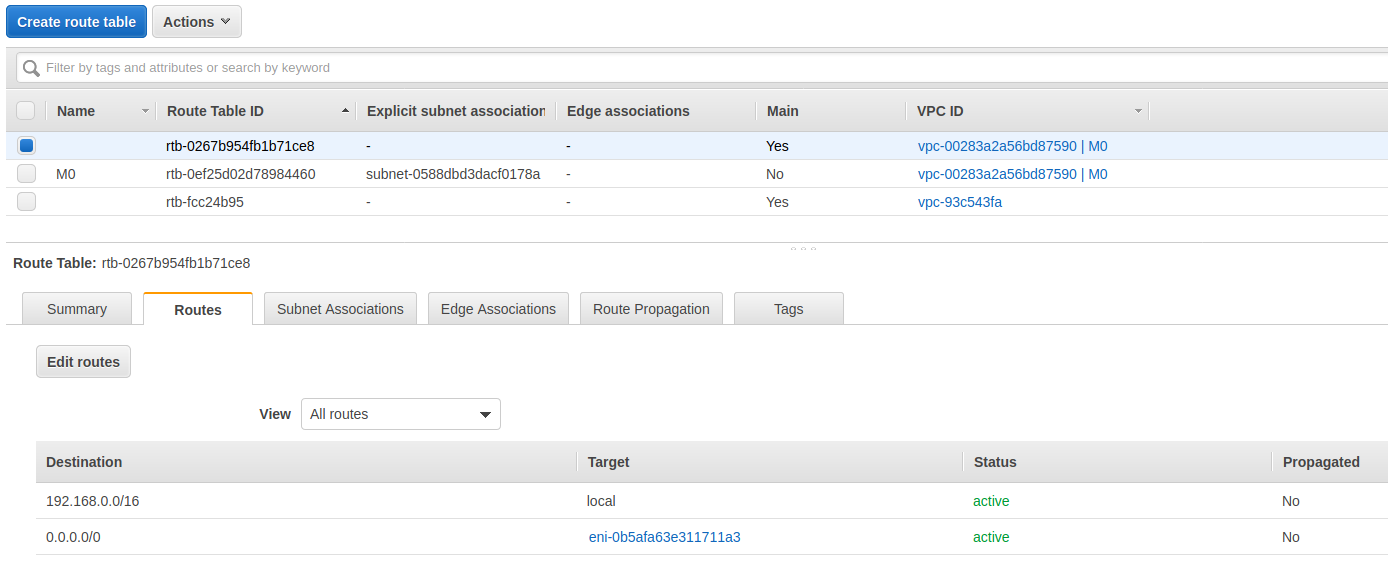
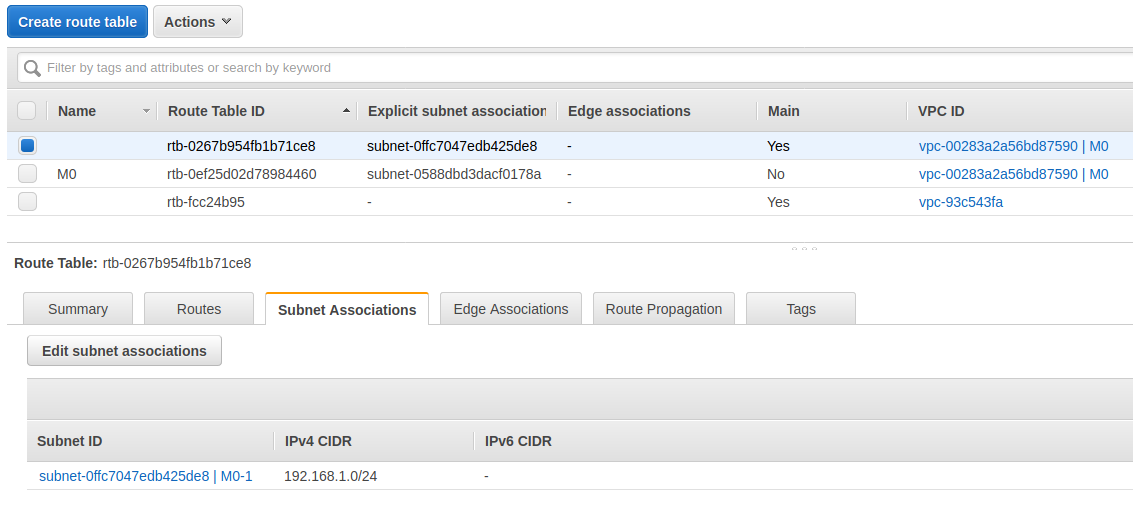
将主路由表关联到 M0-1 子网
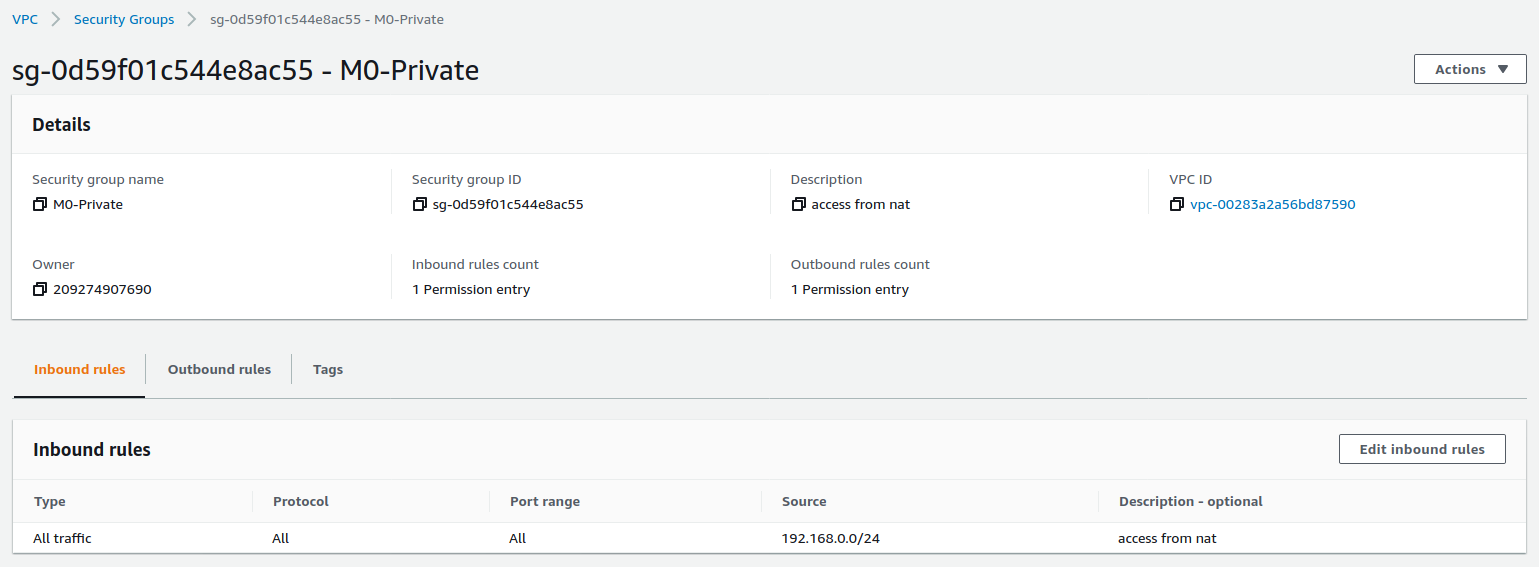
创建私网 Security Group
创建一个私网的 Security Group,允许所有来自 M0-0 子网的所有数据
创建私网实例
创建私网实例,用于 NAT 测试
Network: 选择VPC M0Subnet: 选择M0-1Auto-assign Public IP:Disable
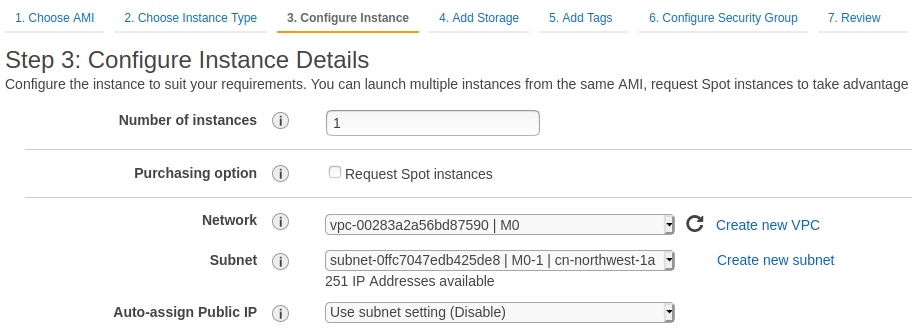
Security Group 选择创建的私网安全组 M0-Private

私网实例详细信息如下
- 私网 IP 地址为 :
192.168.1.64 - 没有公网 IP

从 NAT 实例 M0-0-0 ping M0-1-0
1
2
3
4
5
6
7
8
[ec2-user@ip-192-168-0-6 ~]$ ping 192.168.1.64
PING 192.168.1.64 (192.168.1.64) 56(84) bytes of data.
64 bytes from 192.168.1.64: icmp_seq=1 ttl=64 time=0.495 ms
64 bytes from 192.168.1.64: icmp_seq=2 ttl=64 time=0.451 ms
64 bytes from 192.168.1.64: icmp_seq=3 ttl=64 time=0.442 ms
64 bytes from 192.168.1.64: icmp_seq=4 ttl=64 time=0.476 ms
64 bytes from 192.168.1.64: icmp_seq=5 ttl=64 time=0.486 ms
测试私网实例 M0-1-0
从 NAT 实例 M0-0-0 ssh 进入 M0-1-0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
[ec2-user@ip-192-168-0-6 ~]$ ssh -i ~/.ssh/aws_passed.pem ubuntu@192.168.1.64
The authenticity of host '192.168.1.64 (192.168.1.64)' can't be established.
ECDSA key fingerprint is SHA256:PWhn4SijJrgQzU56d1+5sP/o3BR2/GwRq0JJieClNGU.
ECDSA key fingerprint is MD5:d5:d7:52:8d:0b:11:18:29:e4:1a:55:15:bc:8a:d1:d6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.64' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-1009-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Nov 13 02:23:18 UTC 2020
System load: 0.0 Processes: 99
Usage of /: 16.2% of 7.69GB Users logged in: 0
Memory usage: 18% IPv4 address for eth0: 192.168.1.64
Swap usage: 0%
0 updates can be installed immediately.
0 of these updates are security updates.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
ubuntu@ip-192-168-1-64:~$
测试 M0-1-0 访问外网
1
2
3
4
5
6
7
8
ubuntu@ip-192-168-1-64:~$ ping www.baidu.com
PING www.a.shifen.com (220.181.38.149) 56(84) bytes of data.
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=1 ttl=45 time=21.9 ms
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=2 ttl=45 time=22.0 ms
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=3 ttl=45 time=21.9 ms
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=4 ttl=45 time=22.0 ms
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=5 ttl=45 time=21.9 ms
设置 NAT 端口转发
在 NAT 实例 M0-0-0 设置端口转发: 将 M0-0-0 的 10022 端口上的 TCP 数据转发到 M0-1-0 的 22端口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
[ec2-user@ip-192-168-0-6 ~]$ sudo iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 10022 -j DNAT --to 192.168.1.64:22
[ec2-user@ip-192-168-0-6 ~]$ sudo iptables -t nat -L
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- anywhere anywhere tcp dpt:10022 to:192.168.1.64:22
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- anywhere anywhere
[ec2-user@ip-192-168-0-6 ~]$
在本地开发机器上,通过 NAT实例 M0-0-0 的 10022 端口 SSH 登录 M0-1-0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ ssh -i~/.ssh/aws_passed.pem -p 10022 ubuntu@68.79.5.240
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-1009-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Nov 13 02:33:55 UTC 2020
System load: 0.0 Processes: 99
Usage of /: 16.3% of 7.69GB Users logged in: 0
Memory usage: 18% IPv4 address for eth0: 192.168.1.64
Swap usage: 0%
0 updates can be installed immediately.
0 of these updates are security updates.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Nov 13 02:23:19 2020 from 192.168.0.6
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
ubuntu@ip-192-168-1-64:~$ ping www.baidu.com
PING www.a.shifen.com (220.181.38.150) 56(84) bytes of data.
64 bytes from 220.181.38.150 (220.181.38.150): icmp_seq=1 ttl=45 time=20.6 ms
64 bytes from 220.181.38.150 (220.181.38.150): icmp_seq=2 ttl=45 time=20.7 ms
64 bytes from 220.181.38.150 (220.181.38.150): icmp_seq=3 ttl=45 time=20.8 ms
64 bytes from 220.181.38.150 (220.181.38.150): icmp_seq=4 ttl=45 time=20.7 ms